Scrum is
one of the most popular Agile methodologies. It is an adaptive, iterative,
fast, flexible, and effective methodology designed to deliver significant value
quickly and throughout a project. Scrum ensures transparency in communication
and creates an environment of collective accountability and continuous progress.
The Scrum framework, is structured in
such a way that it supports product and service development in all types of industries
and in any type of project, irrespective of its complexity.
The key
strength of Scrum lies in its use of cross-functional, self-organized, and
empowered teams who divide their work into short, concentrated work cycles
called Sprints
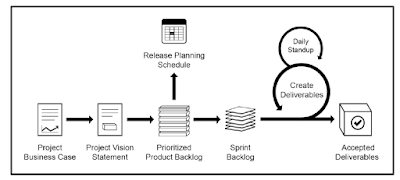
The Scrum
cycle begins with a Stakeholder Meeting, during which the Project Vision is
created. The Product Owner then develops a Prioritized Product Backlog which
contains a prioritized list of business and project requirements written in the
form of User Stories. Each Sprint begins with a Sprint Planning Meeting during which
high priority User Stories are considered for inclusion in the Sprint. A Sprint
generally lasts between one and six weeks and involves the Scrum Team working
to create potentially shippable Deliverables or product increments. During the
Sprint, short, highly focused Daily Standup Meetings are conducted where team
members discuss daily progress. Toward the end of the Sprint, a Sprint Review
Meeting is held during which the Product Owner and relevant stakeholders are
provided a demonstration of the Deliverables. The Product Owner accepts the Deliverables only if they meet the predefined
Acceptance Criteria. The Sprint cycle ends with a Retrospect Sprint Meeting
where the team discusses ways to improve processes and performance as they move forward into
the subsequent Sprint.
Some of
the key benefits of using Scrum in any project are:
- Adaptability—Empirical process control and iterative delivery make projects adaptable and open to incorporating change.
- Transparency—All information radiators like a Scrumboard and Sprint Burndown Chart are shared, leading to an open work environment.
- Continuous Feedback—Continuous feedback is provided through the Conduct Daily Standup, and Demonstrate and Validate Sprint processes.
- Continuous Improvement—The deliverables are improved progressively Sprint by Sprint, through the Groom Prioritized Product Backlog process.
- Continuous Delivery of Value—Iterative processes enable the continuous delivery of value through the Ship Deliverables process as frequently as the customer requires.
- Sustainable Pace—Scrum processes are designed such that the people involved can work at a sustainable pace that they can, in theory, continue indefinitely.
- Early Delivery of High Value—The Create Prioritized Product Backlog process ensures that the highest value requirements of the customer are satisfied first.
- Efficient Development Process—Time-boxing and minimizing non-essential work leads to higher efficiency levels.
- Motivation—The Conduct Daily Standup and Retrospect Sprint processes lead to greater levels of motivation among employees.
- Faster Problem Resolution—Collaboration and colocation of cross-functional teams lead to faster problem solving.
- Effective Deliverables—The Create Prioritized Product Backlog process and regular reviews after creating deliverables ensures effective deliverables to the customer.
- Customer Centric—Emphasis on business value and having a collaborative approach to stakeholders ensures a customer-oriented framework.
- High Trust Environment—Conduct Daily Standup and Retrospect Sprint processes promote transparency and collaboration, leading to a high trust work environment ensuring low friction among employees.
- Collective Ownership—The Approve, Estimate, and Commit User Stories process allows team members to take ownership of the project and their work leading to better quality.
- High Velocity—A collaborative framework enables highly skilled cross-functional teams to achieve their full potential and high velocity.
- Innovative Environment—The Retrospect Sprint and Retrospect Project processes create an environment of introspection, learning, and adaptability leading to an innovative and creative work environment.